Newly discovered by security researchers is a vulnerability known as DoubleClickjacking
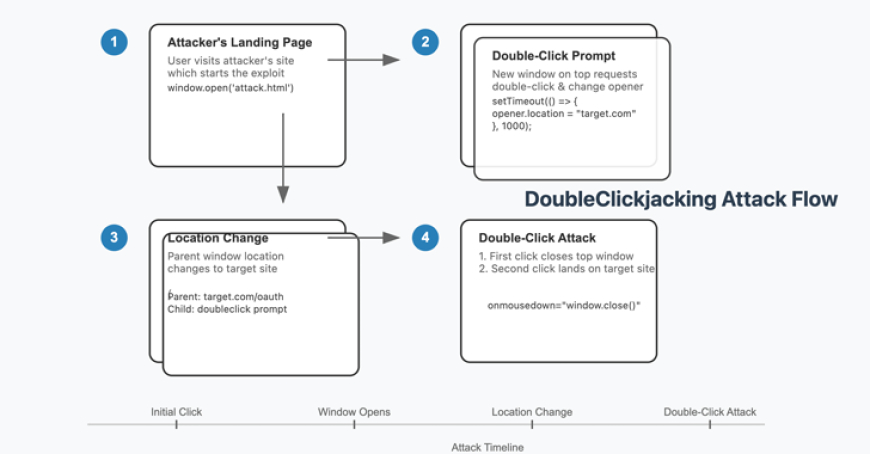
Newly discovered by security researchers is a vulnerability known as DoubleClickjacking. This time-based exploit allows for clickjacking attacks and account takeovers on popular websites. This method, which was uncovered by Paulos Yibelo, allows attackers to evade conventional clickjacking protections by manipulating a double-click sequence instead of a single click. To bypass security measures like X-Frame-Options and SameSite cookies, DoubleClickjacking takes use of the time that passes between the first and second clicks to modify user interface components.
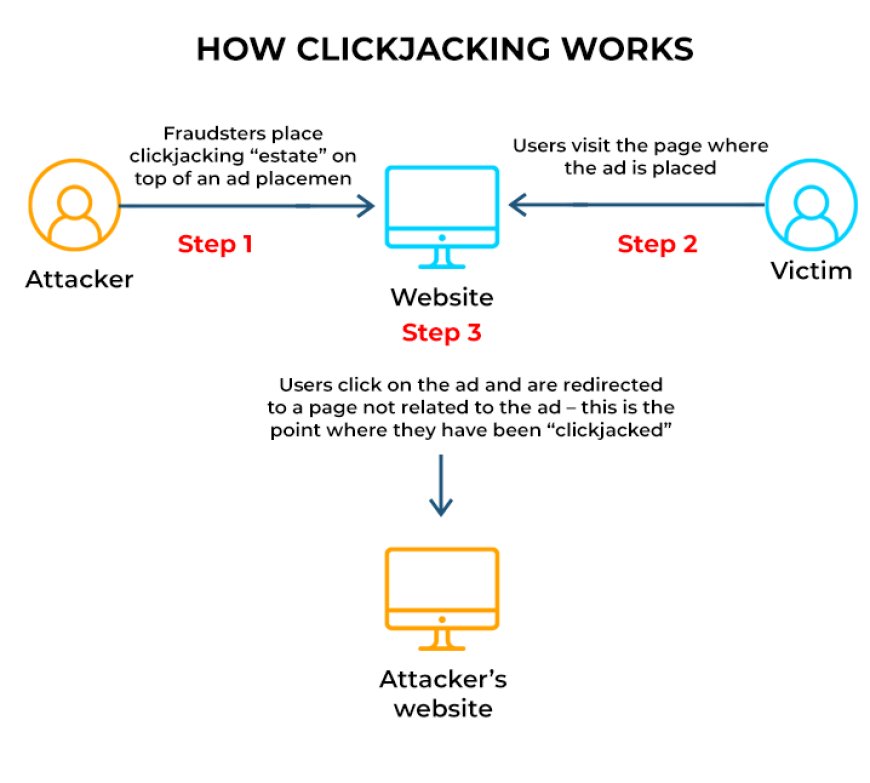
A well-known attack known as clickjacking or UI redressing involves deceiving users into clicking on seemingly innocuous items. This can lead to unintentional activities such as malware distribution or data theft. Expanding on this idea, DoubleClickjacking allows for attacks to be executed with little to no user intervention by timing the user's double clicks.
The following is how the attack unfolds: a malicious website, which the attacker controls, opens a new tab or window that looks like a CAPTCHA or other harmless material. While the user is being asked to double-click, the attacker is utilizing JavaScript to redirect the page to a malicious site. Invisibly authorizing a harmful action (such as providing OAuth rights), the attacker's script closes the original window as the victim clicks.
Content Security Policies (CSP), same-site cookies, and X-frame options are all rendered useless by this novel form of attack. Website owners can protect themselves from this vulnerability by following a practice currently employed by services like Dropbox: disable important buttons by default until a mouse gesture or key hit is detected. It is suggested that browser manufacturers implement new standards to protect against DoubleClickjacking, similar to X-Frame-Options, to stop more exploitation.
This finding, along with last year's gesture-jacking and other increasingly complex attack tactics, highlights the need for improved browser security even more.